What is hybrid cloud? The ultimate guide
A hybrid cloud is a cloud computing environment that uses a mix of on-premises, private cloud and third-party public cloud services with orchestration among these platforms. This environment typically involves a connection from an on-premises data center to a public cloud. The connection can also involve other private assets, including edge devices or additional cloud services, such as storage.
The concept of hybrid cloud computing reflects today's notion that IT resources and services aren't singular or ubiquitous, but rather a complex and dynamic mix of hardware, applications, resources and services. All those varied assets can be operated from many providers and delivered to an enterprise on demand from countless global locations.
This comprehensive guide examines the inner workings of hybrid cloud infrastructures -- their benefits, challenges, applications, use cases, management tools and future trends. Links throughout this page connect to related TechTarget articles providing greater insights, new developments and expert advice critical to planning, implementing and maintaining hybrid cloud in the enterprise.
How do hybrid clouds work?
With hybrid cloud, enterprises deploy workloads in private IT environments or public clouds -- including IaaS, PaaS and SaaS -- and can often move workloads and data between them as computing needs and costs change. This setup provides a business greater flexibility and more data deployment options. Hybrid cloud workloads include the network, hosting and web service features of an application. A typical hybrid cloud can simultaneously involve the following common components:
- Local. One or more applications deployed in a traditional local data center. These local workloads are often mission critical where regulatory or business pressures require the enterprise to exert direct control over the local infrastructure, applications and data.
- Cloud. One or more applications and data stores deployed to a select region (data center) of a public cloud provider. These deployments often reflect less critical or less used workloads and data as well as short-term or experimental deployments. The business manages and interacts with public clouds through the cloud providers' web portals and APIs. It's increasingly common for an enterprise to use more than one public cloud to benefit from each cloud's unique resource or service offerings.
- PaaS and SaaS. One or more applications and data stores hosted by PaaS and SaaS providers. These are often workloads the business needs but chooses not to deploy and operate in-house. Common SaaS examples include HR, accounting, finance, business intelligence and software development toolkits.
All these elements can create a complex web of workloads and data that businesses increasingly struggle to manage cost-effectively.
While the terms are sometimes discussed interchangeably, there are key differences between hybrid and multi-cloud models. A hybrid cloud creates a single environment to operate on-premises private resources, public cloud resources -- such as those offered by Amazon Web Services, Microsoft Azure and Google Cloud Platform -- and the services offered by PaaS and SaaS providers. A multi-cloud environment consists of two or more public cloud providers but doesn't require a private or on-premises component. For instance, a business that deploys certain workloads in AWS and other workloads in Azure is using a multi-cloud strategy.
Hybrid cloud architecture
Establishing a hybrid cloud requires the following four main components:
- At least one public infrastructure as a service (IaaS) platform, such as AWS, Azure or Google.
- Private computing resources, such as an on-premises data center, which typically includes some private cloud capability.
- An adequate network connection to the hybrid cloud's private and public cloud environments.
- A common software platform capable of discovering, operating and managing private and public cloud elements as a unified, highly automated, policy-driven environment.
Hybrid cloud networking
A strong network connection is critical to a successful hybrid cloud strategy. Typically, the connection involves a WAN or dedicated networking service for additional security. A company should consistently evaluate its connection and ensure it meets the bandwidth, latency and uptime (availability) requirements specified in any service-level agreement with a cloud provider.
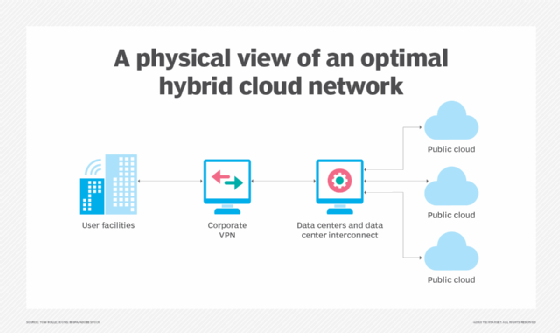
Hybrid cloud integration
An enterprise has no direct control over a SaaS or public cloud (IaaS) architecture. That means a business must adjust its resources, environments, policies and workflows to make them compatible with its chosen public cloud platform's resources, services and APIs. Suitable hardware would need to be implemented in the data center, including servers, storage, a LAN and load balancers. For an effective hybrid arrangement, these on-premises resources and environments must be able to integrate and interoperate with public cloud services and APIs. Cloud providers often supply models and best practices that can accelerate business integration and adoption.
The following are two main approaches to hybrid cloud integration:
- Use the cloud as the front-end application hosting point. This approach essentially relies on one element of the hybrid architecture, such as the public cloud, and uses other resources, such as the data center, for auxiliary or fallback operations. Implementation is often easier and faster, but it poses more limitations on flexibility.
- Create a unified elastic resource pool of data center and cloud functions. This approach endeavors to treat all public and private elements equally from the ground up. It creates a more flexible and ubiquitous hybrid cloud environment but can be more difficult and time-consuming to implement.
Consider the following questions to determine the right integration strategy:
- What are the architecture's complete hybrid integration requirements?
- What combinations of technologies address the integration requirements?
- What's the most appropriate integration style or pattern for the use cases?
- Where does it make sense to deploy the integration platform?
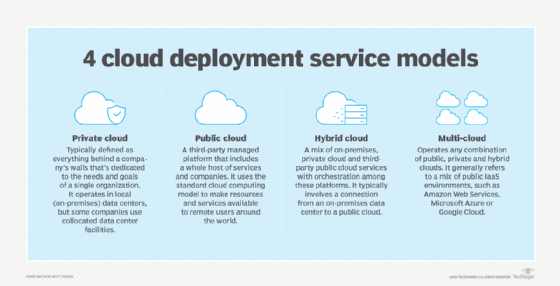
Hybrid cloud platforms
Hybrid cloud architecture traditionally builds a virtualization layer or hypervisor on top of on-premises resources to create and support VMs and, increasingly, container-based workloads. On top of this layer, IT teams install a private cloud software layer, such as VMware Apache CloudStack, OpenNebula or OpenStack, which delivers various cloud capabilities, including self-service access to services, such as compute or database instances; automation and orchestration; resilience; and billing. This layer is integrated into services and APIs from public cloud providers.
A newer hybrid cloud architecture approach involves public cloud providers offering hybrid cloud platforms that extend public cloud services into private data centers. Everything is based on the same software stack. These hybrid cloud platforms connect public and private resources in different ways, but they often incorporate common industry technologies, such as Kubernetes to orchestrate container-based services.
Examples of hybrid cloud platforms include AWS Outposts, Azure Stack, Azure Arc, Azure VMware Solution, Google Anthos, Nutanix Cloud Infrastructure, Nutanix Cloud Clusters, VMware Cloud Foundation and VMware Cloud on AWS.
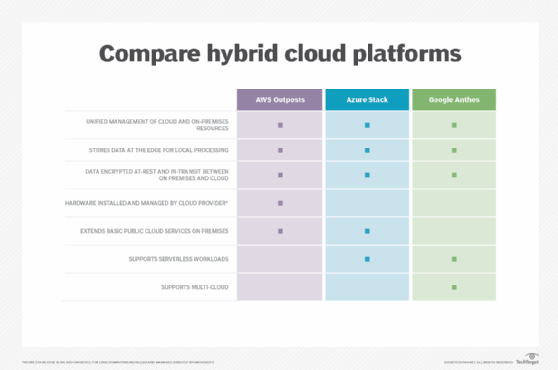
Public cloud vs. private cloud
By definition, the hybrid cloud model includes public cloud and private cloud components.
The public cloud component relies on a third-party provider for on-demand IT resources, such as VMs, applications and storage, as well as services like data analytics, over the internet or a dedicated network. Public cloud providers host workloads and deliver cloud services to multiple organizations.
The private cloud component typically uses on-premises architecture, either in a company's local data center or a separate physical infrastructure provided by a third party, such as Azure Stack. Private clouds can also be based on virtualization software. Whatever the specific private cloud approach, organizations do not share private cloud resources with other users.
There are several tradeoffs to consider between on-premises and cloud computing, including the following:
- Payment structure. Public cloud is priced on a pay-as-you-go model, whereby organizations pay only for the capacity they use, which is typically metered and billed as a monthly fee. But a business that improperly configures its workloads might underutilize and overpay for public cloud services. In contrast, on-premises computing requires a high upfront investment and additional costs, primarily for procurement, installation and maintenance.
- Security. Private cloud users are fully responsible for securing their on-premises environments. They have more control of sensitive data and workloads that reside in their own data center's infrastructure and resources. Public cloud providers and users share security responsibility. The provider typically ensures security of the infrastructure itself, while users must properly secure applications and data inside the cloud. Public cloud users have access to the latest security expertise and tools but are subject to misconfigurations, breaches and other risks of hosting in a shared environment over the public internet.
- Availability. Public cloud providers offer high availability and scalability, but they're not immune to outages that cause downtime across services. Private clouds have their own availability risks. On-premises hardware can break down and require maintenance, and any physical environment is subject to the effects of natural disasters like floods or fires.
Organizations planning a hybrid approach need to consider how they'll move workloads between private and public clouds. Hybrid cloud migration strategies include lift and shift, refactoring and redesign.
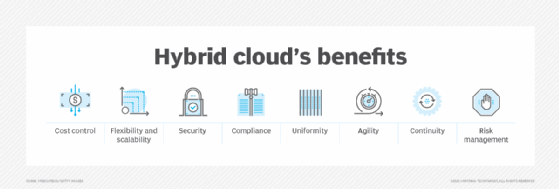
What are the benefits of hybrid cloud?
Hybrid cloud computing enables an enterprise to deploy its most sensitive workloads in an on-premises cloud, connect to workloads and data sources hosted by independent SaaS and PaaS providers and host less critical resources on third-party public cloud PaaS and IaaS providers. This approach provides organizations with the best of private and public cloud models.
The core benefits of hybrid cloud include the following:
- Flexibility. Companies work with various types of data in disparate environments and adjust their infrastructure. A hybrid cloud setup uses traditional systems alongside the latest cloud technology without a full commitment to a single vendor. Organizations can migrate workloads to and from their traditional infrastructure and a vendor's public cloud when necessary.
- Cost management. With a private cloud, organizations own and operate the data center infrastructure, which requires significant capital expense and fixed costs. Alternatively, public cloud resources and services are considered more budget friendly because they're accounted as variable and operational expenses. Hybrid cloud users can choose to run workloads in whichever environment is more secure, reliable and cost-effective.
- Agility and scalability. A hybrid cloud offers more resource options with a public cloud provider versus an organization's physical data center. This capability makes it easier to provision, deploy and scale resources to meet demand spikes. When demand exceeds the capacity of the local data center and private cloud, an organization can burst the application to the public cloud to access extra scale and capacity.
- Resiliency and interoperability. A business can run workloads redundantly in both private and public environments. Components of one workload can also run in both environments and interoperate, such as sharing a common data source.
- Compliance. Organizations in highly regulated industries must follow restrictions on where data can reside, and that often means they can't move certain workloads to the public cloud. With a hybrid cloud model, organizations can keep data in a private environment while operating workloads in the cloud or they can operate workloads in a private data center and move data to and from the public cloud as needed. Companies are able to meet regulatory requirements and still benefit from the cloud's elasticity.
Other hybrid cloud advantages include consistency and support for more standardization in IT management practices.
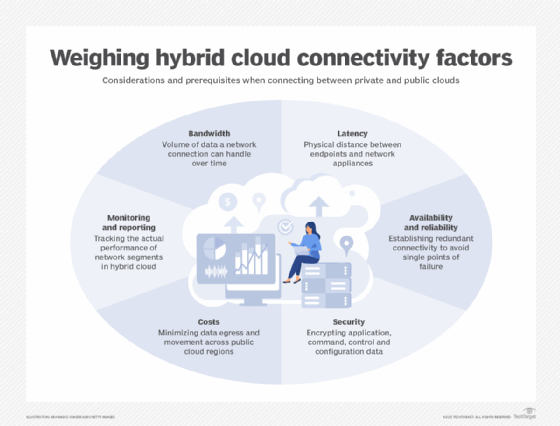
Hybrid cloud challenges
Along with the benefits come hybrid cloud challenges that CIOs must address and resolve, including the following:
- Compatibility. On-premises and public cloud environments work together in a hybrid cloud approach, but they're not fully compatible or easily synchronized. The back-end data center component of a hybrid cloud application, for example, can't respond as quickly as the front-end public cloud component, causing latency problems and other complexities.
- Data handling. Improper data placement and movement in a hybrid cloud can create security and cost challenges. To secure data in transit, businesses need to encrypt all traffic. They should also populate data in the right environment to avoid moving data across cloud environments and triggering cloud network and egress fees. Additionally, necessary workloads should reside in public cloud storage to avoid unnecessary transfers and prevent spikes in charges.
- Complex access management. Authentication and authorization are among the more significant hybrid cloud security challenges. Organizations must adopt centralized protocols to access data in private and public cloud environments. Use identity and access management and single sign-on tools. Assign permissions only when necessary to simplify access management. Configuration errors, poor regulatory or compliance implementation, lack of patches and other vital software maintenance, and other oversights can all contribute to data security gaps in hybrid clouds.
- Network dependence. A hybrid cloud is critically dependent on access such as internet connectivity, placing enormous demands on WAN availability, bandwidth and latency. Any network disruption or outage will effectively halt hybrid cloud operation. Businesses must implement adequate WAN resources and plan for backup WAN connectivity.
- Skills gap. Hybrid cloud adoption requires users and IT staff to possess a specific set of technical skills. The expertise needed for public cloud infrastructure and services differs from what's required for a private data center, and the learning curve to close that skills gap can lead to human error. Businesses might need to hire additional IT staff for private cloud implementation and hybrid cloud operations.
- Private cloud maintenance. A hybrid cloud's on-premises or private cloud component requires substantial investment, maintenance and expertise, since it's essentially a dedicated part of the local data center. Implementation of additional software, such as databases, help desk systems and other tools, can further complicate a private cloud. Proper data planning, public cloud security tools and investment in employee training, and cloud certifications can smooth hybrid cloud adoption.

Hybrid cloud security
Underpinning all hybrid cloud challenges in one form or another are security issues that inherently surround publicly accessible cloud environments and the transfer of sensitive workloads across distributed clouds.
Single hybrid cloud is now multiple clouds, said IBM cloud security architect Mark Buckwell during the RSA Conference in April 2023, pointing to the reticence of businesses to fully trust their precious assets residing up there. "They still don't want to move the crown jewels of the organization off premise into cloud," Buckwell said, "so we end up integrating different parts of an application with different components, sitting on different technologies… And that just makes the whole solution a lot more complex because now we have data flowing in all sorts of different places."
Top-of-mind issues for chief information security officers (CISOs) include a centralized security architecture, vendor compatibility and accountability, technology integration, API exposure, visibility and governance. And most of all, CISOs need to meet business goals and compliance edicts by ensuring on-premises security controls and processes coexist with native-cloud technologies.
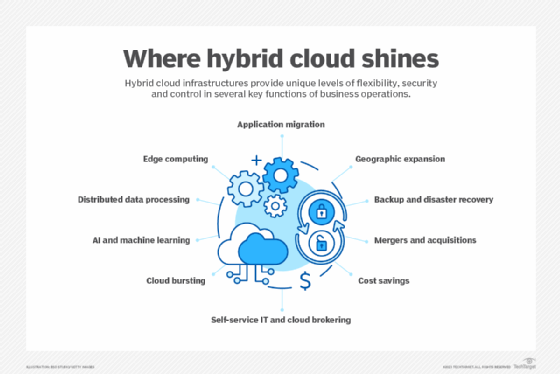
What are hybrid cloud use cases?
Before implementing a hybrid cloud infrastructure, first consider several hybrid cloud use cases and their advantages, disadvantages and remedies to determine whether this architecture fits the company's IT and business needs. The following are some of the more common hybrid cloud use cases to evaluate:
- Digital transformation. Companies often want to modernize their IT infrastructure through public cloud adoption, but legacy applications or compliance factors can preclude a business from entirely shutting down a private data center. Hybrid cloud enables companies with mixed data and application types to migrate parts of their IT infrastructure to the cloud and retain some applications on premises.
- Application migration. Hybrid clouds provide secure and proven landing zones, enable selection of the best cloud environment depending on the type of workload and improve the maintenance of code updates. However, old applications might not be good migration candidates.
- Development and testing. It's cheaper and faster to develop and test applications in the public cloud because there's no need to purchase and set up on-premises physical hardware. Software developers routinely use public cloud platforms and other cloud services, such as storage, to host development projects.
- Cloud bursting. Hybrid clouds provide flexibility for workloads when there's a need for extra capacity, especially in use cases like unpredictable burst workloads, data processing, media processing and seasonal retail bursting. But cloud bursting must be carefully executed to avoid latency when moving data.
- Distributed data processing. When workloads are distributed across different locations, hybrid cloud environments provide access to data and applications stored on premises and off site, speed processing times and reduce latency without extensive local infrastructure. Nonetheless, maintaining consistency across distributed data sets can be challenging without encryption and access controls.
- Backup and disaster recovery. A hybrid cloud helps organizations replicate on-premises workloads and back up data in the cloud. If there's a disruption in the data center, workloads fail over to the cloud environment and operate properly via on-demand cloud resources. Careful implementation is necessary to avoid hybrid cloud backup challenges.
- AI and machine learning. Building generative AI large language models (LLMs) on premises can be costly and require highly skilled talent. A hybrid cloud setup can help enterprises adapt to recent technology advancements and apply the most cost-effective hardware. Still, developing and running AI workloads on a hybrid cloud through publicly available clouds can introduce new security, privacy and data management issues.
- Edge computing. Using edge computing in a hybrid cloud environment enables businesses to more readily stage data-intensive and time-sensitive tasks closer to the source, reducing latency, easing networking requirements and improving data protection. Maintaining security in distributed environments, however, might require zero-trust architectures and additional management techniques.
- Mergers and acquisitions. Integration of data and applications from the old entity to the new entity is key when following through on a merger or acquisition. "Most major IT cleanups involved mergers that were never integrated and, ultimately, became a backpack of rocks," said Infosys consultant Mike Fitzgerald. Hybrid cloud can better address differences in functions such as HR, ERP, CRM and transactional systems. Still, IT will have to cope with the complexities created by different hardware, platforms and application infrastructures.
Hybrid cloud management tools
Hybrid cloud architecture comprises multiple environments and types of components, making hybrid cloud management a complex task. Fortunately, there are strategies and tools to help resolve the complications of hybrid management and create a streamlined approach across environments.
Implement hybrid cloud management practices to maximize control of distributed environments. For example, to create a consistent, unified approach across the various components, establish a cloud governance policy that defines standard processes for resource configurations, access control and other important operations.
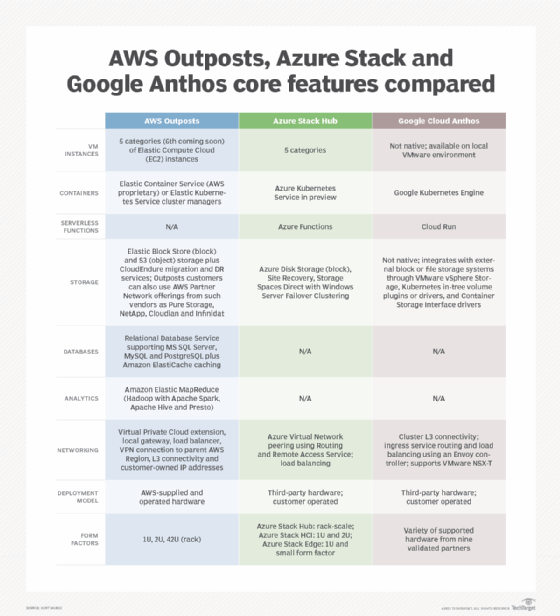
Management tools geared to increasingly distributed cloud environments can centralize the deployment and administration of data, applications and workloads across hybrid architectures that mix private infrastructure with public cloud resources. They include the following:
- A new generation of frameworks for the creation of hybrid clouds, including Azure Stack, Azure Arc, AWS Outposts and Google Cloud Anthos.
- More conventional management platforms for hybrid cloud, such as VMware Cloud Foundation and Cisco Intersight.
- Services like Elastic Kubernetes Service Anywhere to manage workloads deployed on private infrastructure using Amazon's managed Kubernetes service.
Centralized control of on-premises and cloud-based resources with a hybrid cloud management tool set provide cost and performance monitoring, security, reporting and analytics. Hybrid cloud management tools include CloudBolt, Embotics, Flexera Cloud Management Platform, IBM Turbonomic, Morpheus Data, Nutanix Cloud Manager Cost Governance (formerly Beam) and Scalr. Explore and test different features within your environment to choose the hybrid cloud management tool that suits your organization's particular hybrid architecture needs.
Infrastructure-as-code tools can also help manage hybrid deployment. Ansible, Chef, HashiCorp's Terraform, Puppet and Salt, for example, all provide hybrid cloud management capabilities. Adopting containers and Kubernetes orchestration is another way to unify and seamlessly migrate the resources in a hybrid architecture.
For secure movement of workloads across environments, vendors such as Microsoft and Palo Alto Networks provide cloud security posture management tools that automate risk management and compliance requirements to continuously monitor cloud-based systems for vulnerabilities and misconfigurations.
What's in store for hybrid cloud?
As with most advanced technologies, hybrid cloud infrastructure, tools and services are rapidly evolving and expanding. For companies modernizing their business operations, hybrid cloud's embrace of AI, edge computing and integration promises unique levels of flexibility, security and control. But moving data, applications and workloads across distributed cloud environments increases complexity as well as modernization costs. New control planes in hybrid cloud tools provide some relief by improving all aspects of management in the cloud and on premises.
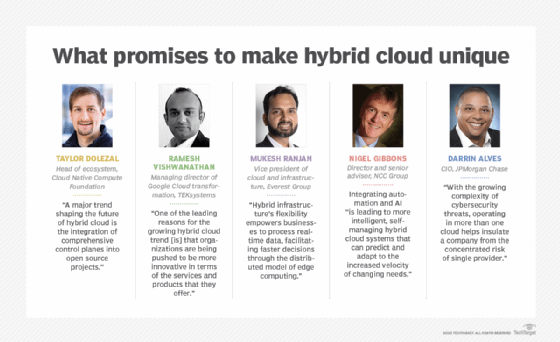
Following are some of the top hybrid cloud trends in 2024 and beyond as seen by industry veterans:
- Comprehensive control planes integrated into open source projects. These new platforms can be used for building and running cloud-native applications and provide a secure way to manage cloud resources in various environments.
- Increased hybrid cloud deployments to optimize latency-sensitive tasks. "Hybrid infrastructure's flexibility empowers businesses to process real-time data, facilitating faster decisions through the distributed model of edge computing," said the Everest Group's Mukesh Ranjan.
- Higher levels of integration of automation, AI and machine learning into hybrid cloud environments. "This trend is leading to more intelligent, self-managing hybrid cloud systems that can predict and adapt to the increased velocity of changing needs," explained NCC Group's Nigel Gibbons.
- Synergistic relationship between generative AI initiatives and hybrid cloud models. Rather than build LLMs in-house, many organizations are enlisting publicly available models trained by cloud providers.
- Greater adoption of language-agnostic, open source platforms. These platforms can simplify cloud application management, support different application architectures and add more flexibility to hybrid cloud.
- Distributed cloud environments to better address cybersecurity threats. "[O]perating in more than one cloud helps insulate a company from the concentrated risk of single provider," said Darrin Alves of JPMorgan Chase.
- Cost optimization to balance application modernization expenses with the bottom line. With limited modernization choices on premises, finding the right mix of providers and features in a hybrid cloud environment can help businesses optimize costs and speed their digital transformation efforts.
Stephen J. Bigelow, senior technology editor at TechTarget, has more than 20 years of technical writing experience in the PC and technology industry. Ron Karjian is an industry editor and writer at TechTarget covering business analytics, artificial intelligence, data management, security and enterprise applications.
Sarah Neenan contributed to this article.






