cloud security
Cloud security, also known as cloud computing security, is the practice of protecting cloud-based data, applications and infrastructure from cyber attacks and cyber threats.
Cybersecurity, of which cloud security is a subset, has the same goals. Where cloud security differs from traditional cybersecurity is in the fact that administrators must secure assets that reside within a third-party service provider's infrastructure.
Why cloud security is important
As enterprise cloud adoption grows, business-critical applications and data migrate to trusted third-party cloud service providers (CSPs). Most major CSPs offer standard cybersecurity tools with monitoring and alerting functions as part of their service offerings, but in-house information technology (IT) security staff may find these tools do not provide enough coverage, meaning there are cybersecurity gaps between what is offered in the CSP's tools and what the enterprise requires. This increases the risk of data theft and loss.
Because no organization or CSP can eliminate all security threats and vulnerabilities, business leaders must balance the benefits of adopting cloud services with the level of data security risk their organizations are willing to take.
This article is part of
What is cloud security management? Guide and best practices
Putting the right cloud security mechanisms and policies in place is critical to prevent breaches and data loss, avoid noncompliance and fines, and maintain business continuity (BC).
A major benefit of the cloud is that it centralizes applications and data and centralizes the security of those applications and data as well. Eliminating the need for dedicated hardware also reduces organizations' cost and management needs, while increasing reliability, scalability and flexibility.
How cloud security works
Cloud computing operates in three main environments:
- Public cloud services are hosted by CSPs. These include software as a service (SaaS), platform as a service (PaaS) and infrastructure as a service (IaaS).
- Private clouds are hosted by or for a single organization.
- Hybrid clouds include a mix of public and private clouds.
As a result, cloud security mechanisms take two forms: those supplied by CSPs and those implemented by customers. It is important to note that handling of security is rarely the complete responsibility of the CSP or the customer. It is usually a joint effort using a shared responsibility model.
The shared responsibility model
Although not standardized, the shared responsibility model is a framework that outlines which security tasks are the obligation of the CSP and which are the duty of the customer. Enterprises using cloud services must be clear which security responsibilities they hand off to their provider(s) and which they need to handle in-house to ensure they have no gaps in coverage.
Customers should always check with their CSPs to understand what the provider covers and what they need to do themselves to protect the organization.
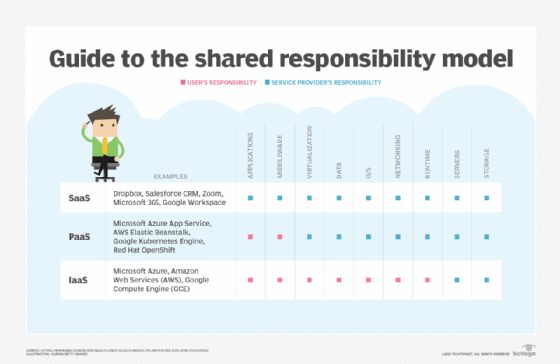
CSP security responsibilities
Security controls supplied by CSPs vary by service model, be it SaaS, PaaS or IaaS. Customer responsibility commonly increases from SaaS to PaaS to IaaS.
In general, CSPs are always responsible for servers and storage. They secure and patch the infrastructure itself, as well as configure the physical data centers, networks and other hardware that power the infrastructure, including virtual machines (VMs) and disks. These are usually the sole responsibilities of CSPs in IaaS environments.
In a PaaS environment, CSPs assume more responsibility, including securing runtime, networking, operating systems (OSes), data and virtualization. In a SaaS environment, CSPs also provide application and middleware security.
The details of security responsibilities can vary by provider and customer. For example, CSPs with SaaS-based offerings may or may not offer customers visibility into the security tools they use. IaaS providers, on the other hand, usually offer built-in security mechanisms that enable customers to access and view CSP security tools, which may also provide customer-alerting functionality.
Customer security responsibilities
To supplement the CSP security controls listed above, customers are generally responsible for application, middleware, virtualization, data, OS, network and runtime security in IaaS clouds. In IaaS architectures, such as Amazon Virtual Private Cloud (VPC) or Microsoft Azure Virtual Network (VNet), for example, customers can supplement, replace or overlay built-in cybersecurity mechanisms with their own set of tools.
In PaaS environments, customers take on fewer security tasks, generally only application and middleware security. SaaS environments involve even less customer responsibility.
Data security and identity and access management (IAM) are always the responsibility of the customer, however, regardless of cloud delivery model. Encryption and compliance are also the responsibility of the customer.
Yet, because CSPs control and manage the infrastructure customer apps and data operate within, adopting additional controls to further mitigate risk can be challenging. IT security staff should get involved as early as possible when evaluating CSPs and cloud services. Security teams must evaluate the CSP's default security tools to determine whether additional measures will need to be applied in-house.
Adding a company's own security tools to cloud environments is typically done by installing one or more network-based virtual security appliances. Customer-added tool sets enable security administrators to get granular with specific security configurations and policy settings. Many enterprises also often find it cost-effective to implement the same tools in their public clouds as they have within their corporate local area networks (LANs). This prevents administrators from having to recreate security policies in the cloud using disparate security tools. Instead, a single security policy can be created once and then pushed out to identical security tools, regardless of whether they are on premises or in the cloud.
Cloud security tools
Many of the same tools used in on-premises environments should be used in the cloud, although cloud-specific versions of them may exist. These tools and mechanisms include encryption, IAM and single sign-on (SSO), data loss prevention (DLP), intrusion prevention and detection systems (IPSes/IDSes) and public key infrastructure (PKI).
Some cloud-specific tools include the following:
- Cloud workload protections platforms (CWPPs). A CWPP is a security mechanism designed to protect workloads -- for example, VMs, applications or data -- in a consistent manner.
- Cloud access security brokers (CASBs). A CASB is a tool or service that sits between cloud customers and cloud services to enforce security policies and, as a gatekeeper, add a layer of security.
- Cloud security posture management (CSPM). CSPM is a group of security products and services that monitor cloud security and compliance issues and aim to combat cloud misconfigurations, among other features.
Secure Access Service Edge (SASE) and zero-trust network access (ZTNA) are also emerging as two popular cloud security models/frameworks.
Security as a Service, often shortened to SaaS or SECaaS, is a subset of software as a service. The Cloud Security Alliance (CSA) defined 10 SECaaS categories:
- IAM
- DLP
- web security
- email security
- security assessments
- intrusion management
- security information and event management (SIEM)
- encryption
- BC/disaster recovery (BCDR)
- network security
These include services such as firewall as a service, cloud-based virtual private networks (VPNs) and key management as a service (KMaaS).
How to secure data in the cloud
The steps required to secure data in the cloud vary. Factors, including the type and sensitivity of the data to be protected, cloud architecture, accessibility of built-in and third-party tools, and number and types of users authorized to access the data must be considered.
Some general best practices to secure business data in the cloud include the following:
- Encrypt data at rest, in use and in motion.
- Use two-factor authentication (2FA) or multifactor authentication (MFA) to verify user identity before granting access.
- Adopt cloud edge security protections, including firewalls, IPSes and antimalware.
- Isolate cloud data backups to prevent ransomware threats.
- Ensure data location visibility and control to identify where data resides and to implement restrictions on whether data can be copied to other locations inside or outside the cloud.
- Log and monitor all aspects of data access, additions and changes.
Emerging cybersecurity tools should also be considered to help secure data in clouds. These include network detection and response (NDR) and artificial intelligence (AI) for IT operations (AIOps). Both tools collect cloud infrastructure health and cybersecurity information. AI then analyzes data and alerts administrators of abnormal behavior that could indicate a threat.
Top cloud security challenges
Many of the traditional cybersecurity challenges also exist in the cloud. These can include the following:
- insider threats
- data loss
- data breaches
- IAM
- key management
- access control
- phishing
- malware
- shadow IT
- distributed denial-of-service (DDoS) attacks
- insecure application programming interfaces (APIs)
As for cloud security challenges specifically, administrators have to deal with issues that include the following:
- cloud account hijacking;
- lack of cloud visibility and control;
- working with cloud security tools that in-house administrators may be unfamiliar with;
- tracking and monitoring where data is located both in transit and at rest;
- misconfigurations;
- weak cloud control plane;
- challenges understanding the shared responsibility model;
- nefarious use of cloud services;
- multi-tenancy concerns;
- incompatibilities with on-premises environments;
- cloud compliance; and
- cloud governance.
Security administrators must have plans and processes in place to identify and curb emerging cloud security threats. These threats typically revolve around newly discovered exploits found in applications, OSes, VM environments and other network infrastructure components. To handle these security challenges and eliminate emerging threats, organizations must quickly and properly update and patch software that they control.
It's also important to establish communications channels between in-house IT and CSP staff. In-house staff should subscribe to, monitor and digest the CSP's security bulletin stream. If coordination between the customer and CSP is required to handle a security incident, well-documented communications channels must be established and continuously updated so time isn't wasted when working through a security breach.
Cloud security best practices
There are separate SaaS best practices, PaaS best practices and IaaS best practices. Organizations should also adhere to a number of general cloud security best practices, including the following:
- Understand the shared responsibility model, including the responsibilities of your CSPs and your security team.
- Choose your CSPs wisely. Know what security controls they offer, and review contracts and service-level agreements (SLAs) diligently.
- Adopt a strong, granular IAM policy to control who has access to what. Employ the principle of least privilege (POLP), and require strong passwords and 2FA or MFA.
- Encrypt data in at rest, in use and in motion.
- Maintain cloud visibility through continuous monitoring.
- Understand cloud compliance requirements and regulations.
- Establish and enforce cloud security policies.
- Conduct security awareness training for employees, third-party partners and anyone accessing organizational cloud resources.
- Segment clouds and workloads.







