distributed denial-of-service (DDoS) attack
What is a DDoS attack?
In a distributed denial-of-service (DDoS) attack, multiple compromised computer systems attack a target and cause a denial of service for users of the targeted resource. The target can be a server, website or other network resource. The flood of incoming messages, connection requests or malformed packets to the target system forces it to slow down or even crash and shut down, thereby denying service to legitimate users or systems.
Many types of threat actors, ranging from individual criminal hackers to organized crime rings and government agencies, carry out DDoS attacks. In certain situations -- often ones related to poor coding, missing patches or unstable systems -- even legitimate, uncoordinated requests to target systems can look like a DDoS attack when they are just coincidental lapses in system performance.
How do DDoS attacks work?
In a typical DDoS attack, the assailant exploits a vulnerability in one computer system, making it the DDoS master. The attack master system identifies other vulnerable systems and gains control of them by infecting them with malware or bypassing the authentication controls through methods like guessing the default password on a widely used system or device.
A computer or network device under the control of an intruder is known as a zombie, or bot. The attacker creates what is called a command-and-control server to command the network of bots, also called a botnet. The person in control of a botnet is referred to as the botmaster. That term has also been used to refer to the first system recruited into a botnet because it is used to control the spread and activity of other systems in the botnet.
Botnets can be composed of almost any number of bots; botnets with tens or hundreds of thousands of nodes have become increasingly common. There may not be an upper limit to their size. Once the botnet is assembled, the attacker can use the traffic generated by the compromised devices to flood the target domain and knock it offline.
The target of a DDoS attack is not always the sole victim because DDoS attacks involve and affect many devices. The devices used to route malicious traffic to the target may also suffer a degradation of service, even if they aren't the main target.

Types of DDoS attacks
There are three main types of DDoS attacks:
- Network-centric or volumetric attacks. These overload a targeted resource by consuming available bandwidth with packet floods. An example of this type of attack is a domain name system amplification attack, which makes requests to a DNS server using the target's Internet Protocol (IP) address. The server then overwhelms the target with responses.
- Protocol attacks. These target network layer or transport layer protocols using flaws in the protocols to overwhelm targeted resources. A SYN flood attack, for example, sends the target IP addresses a high volume of "initial connection request" packets using spoofed source IP addresses. This drags out the Transmission Control Protocol handshake, which is never able to finish because of the constant influx of requests.
- Application layer. Here, the application services or databases get overloaded with a high volume of application calls. The inundation of packets causes a denial of service. One example of this is an Hypertext Transfer Protocol (HTTP) flood attack, which is the equivalent of refreshing many webpages over and over simultaneously.
Internet of things and DDoS attacks
The devices constituting the internet of things (IoT) may be useful to legitimate users, but in some cases, they are even more helpful to DDoS attackers. The IoT-connected devices include any appliance with built-in computing and networking capacity, and all too often, these devices are not designed with security in mind.
IoT-connected devices expose large attack surfaces and often pay minimal attention to security best practices. For example, devices are often shipped with hardcoded authentication credentials for system administration, making it simple for attackers to log in to the devices. In some cases, the authentication credentials cannot be changed. Devices also often ship without the capability to upgrade or patch the software, further exposing them to attacks that use well-known vulnerabilities.
IoT botnets are increasingly being used to wage massive DDoS attacks. In 2016, the Mirai botnet was used to attack the domain name service provider Dyn; attack volumes were measured at over 600 gigabits per second. Another late 2016 attack unleashed on OVH, the French hosting firm, peaked at more than 1 terabit per second. Many IoT botnets since Mirai use elements of its code. The dark_nexus IoT botnet is one example.
Identifying DDoS attacks
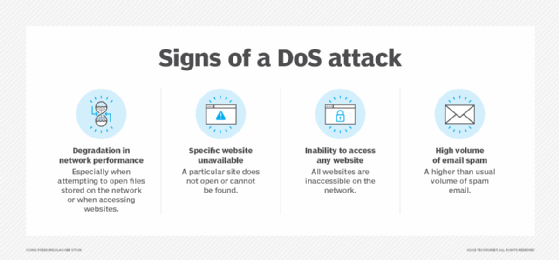
DDoS attack traffic essentially causes an availability issue. Availability and service issues are normal occurrences on a network. It's important to be able to distinguish between those standard operational issues and DDoS attacks.
Sometimes, a DDoS attack can look mundane, so it is important to know what to look for. A detailed traffic analysis is necessary to first determine if an attack is taking place and then to determine the method of attack.
Examples of network and server behaviors that may indicate a DDoS attack are listed below. One or a combination of these behaviors should raise concern:
- One or several specific IP addresses make many consecutive requests over a short period.
- A surge in traffic comes from users with similar behavioral characteristics. For example, if a lot of traffic comes from users of a similar devices, a single geographical location or the same browser.
- A server times out when attempting to test it using a pinging service.
- A server responds with a 503 HTTP error response, which means the server is either overloaded or down for maintenance.
- Logs show a strong and consistent spike in bandwidth. Bandwidth should remain even for a normally functioning server.
- Logs show traffic spikes at unusual times or in a usual sequence.
- Logs show unusually large spikes in traffic to one endpoint or webpage.
These behaviors can also help determine the type of attack. If they are on the protocol or network level-- for example, the 503 error -- they are likely to be a protocol-based or network-centric attack. If the behavior shows up as traffic to an application or webpage, it may be more indicative of an application-level attack.
In most cases, it is impossible for a person to track all the variables necessary to determine the type of attack, so it is necessary to use network and application analysis tools to automate the process.
DDoS defense and prevention
DDoS attacks can create significant business risks with lasting effects. Therefore, it is important to understand the threats, vulnerabilities and risks associated with DDoS attacks.
Once underway, it is nearly impossible to stop these attacks. However, the business impact of these attacks can be minimized through some core information security practices. These include performing ongoing security assessments to look for and resolve DoS-related vulnerabilities and using network security controls, including services from cloud service providers specializing in responding to DDoS attacks.
In addition, solid patch management practices, email phishing testing and user awareness, and proactive network monitoring and alerting can help minimize an organization's contribution to DDoS attacks across the internet.
Examples of DDoS attacks
Besides the IoT-based DDoS attacks mentioned earlier, other recent DDoS attacks include the following:
- A 2018 attack on GitHub is said to be the biggest DDoS attack to date. The attack sent massive amounts of traffic to the platform, which is used by millions of developers to post and share code.
- A volumetric DDoS attack targeted New Zealand's Exchange in 2020, forcing it to go offline for several days.
- In 2019, China's Great Cannon DDoS operation targeted a website used to organize pro-democracy protests in Hong Kong, causing traffic congestion on the site. DDoS attacks are often used in social movements, not just by hackers, but also by hacktivists and government-affiliated organizations. DDoS attacks are a good way to direct public attention at a specific group or cause.
- Also in 2020, threat actor groups Fancy Bear and Armada Collective threatened several organizations with DDoS attacks unless a bitcoin ransom was paid. This is an example of how DDoS attacks and ransomware are used in tandem.
Although DDoS attacks are relatively cheap and easy to implement, they vary widely in complexity and can have a severe impact on the businesses or organizations targeted. Learn how businesses can prevent these attacks by buying a service from an internet service provider, using a content delivery network and deploying an in-house intrusion prevention system.






