6 cloud governance framework principles and challenges
An organization that wants to control its cloud environment should examine how well it adheres to these key pillars of cloud governance.
Cloud computing delivers faster, more agile responses to changing business demands than previous ways used to deliver IT services. Along with these and other numerous benefits, the cloud also introduces a significant risk: the loss of control. This can lead to cost overruns, inefficient use of cloud resources, security breaches, data leaks and failure to meet compliance obligations.
Good governance practices mitigate those risks. A cloud governance framework defines how to control key management points in cloud operations. It also helps set boundaries across potentially competing interests in an organization.
What is cloud governance, and why is it important?
Cloud governance is a set of practices that help ensure users operate in the cloud in ways that they want, that the operations are efficient, and that the user can monitor and correct operations as needed. A cloud governance framework is not a new set of concepts or practices, but simply the application of existing governance practices to cloud operations.
What are the principles of cloud governance?
A cloud management strategy must incorporate several key aspects of cloud governance. Consider them essential to institute proper controls and optimize the use of cloud services:
This article is part of
What is cloud management? Definition, benefits and guide
- financial management
- operations management
- security and compliance management
- data management
- performance management
- asset and configuration management
These elements are not independent, isolated objectives, however -- they influence and, in some cases, constrain each other. Data management and security are interwoven. Operations management and cost controls overlap and influence each other, while operations management also helps shape how an enterprises implements data lifecycle management policies. Developers and product managers can choose a specialized data loss protection service to boost security; although, at scale, this service can be prohibitively expensive.
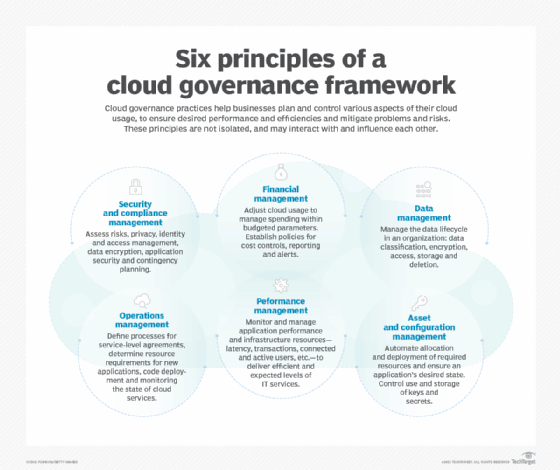
Let's walk through each of the cloud governance framework aspects and how to accomplish them.
1. Security and compliance management
Cloud governance includes the same security topics found in any enterprise security effort: risk assessment, identity and access management, data encryption and key management, application security, contingency planning, and many other areas. From a governance perspective, the objectives of information security practices are shaped by a combination of business objectives and regulations.
As you formulate information security practices, understand that you'll need to choose tradeoffs between business expediency and security risks. For example, you can attempt to eliminate all moderate and severe vulnerabilities in your applications, but you'll have to shift IT resources from developing new features to remediating code vulnerabilities. Balance product development and other business considerations with the government and security regulations that apply to your business.
A governance model should build on existing governance policies and frameworks, including cybersecurity, privacy and risk management. For example, National Institute of Standards and Technology (NIST) cybersecurity resources point to frameworks for those three. Also, take advantage of your public cloud provider's specialized security services to mitigate the risk of data leaks, denial-of-service attacks and other common threats.
2. Financial management
An unwelcome rite of passage in enterprise IT is to survive the first explosively high cloud computing bill. Cloud service providers and advocates rightly argue that cloud services make more financial sense than buying and managing your own infrastructure. That's true, only if you effectively control your cloud costs with diligent policies and reporting.
Financial management policies provide a framework to make business decisions about cloud resources. For example, an organization uses managed services as much as possible to reduce the cost of operational overhead. Another business defines a checklist of cost management steps to follow before deploying a new service to a public cloud.
Budgets are well understood, but it can be difficult to estimate costs because the detailed information you need is often distributed across multiple services. For example, a billing summary may have subtotals for object storage, but details about the contents stored in those systems are found only in the storage service itself. To calculate the total cost, a business might need to search across regions, accounts and various cloud services.
Develop a plan to gather information to create and track budgets. Most cloud vendors provide cost reporting tools. If those do not meet your needs, look to third-party services to fill that gap.
Set up realistic policies around cost alerts. If your cloud environment exceeds 50% of its budget just a few days into the month, an alert gives you time to adjust your infrastructure and service use. Many alerts reflect real-time use and spending, but others may arrive after you've breached a spending threshold, so create budget and policies that give you extra flexibility.
3. Operations management
The focus of operations management is to control how cloud resources deliver services. Consider the following action items:
- define rules and processes that control how to create new applications or workloads that run in the cloud;
- set service-level agreements (SLAs) to allocate resources;
- deploy application code to various environments, particularly production environments; and
- monitor the state of services to ensure SLAs are met.
Perhaps a developer or product manager will ask, "How can we deliver this new application to our customers?" The answer should be found in a well-defined operations policy, and should include the following:
- how to coordinate with the operations team;
- how to specify identity and access management requirements;
- how to estimate compute, storage and network requirements; and
- how to meet monitoring and logging requirements.
Moreover, a clear, well-defined operations management practice is one of the best ways to prevent shadow IT operations from creeping into your cloud environment. Good cost monitoring and performance monitoring can also help identify when cloud resources are deployed outside of normal operating procedures.
4. Data management
As the ability to collect, store and analyze data expands, so does the difficulty to effectively manage that data. Your governance strategy and practices should include clear guidance to manage the full lifecycle of data in your organization.
Begin with a data-classification scheme. Not all data is equally valuable or needs comparable levels of security. Sensitive and confidential data warrant more security controls than public information. The best practice for data in the cloud is to encrypt all data in transit and at rest -- consider this your default behavior. Other controls, such as who can access or update particular data types, will vary according to the data classification and functional requirements around how the data is used.
Governance policies help data owners, product managers and application developers understand how to protect data based on its classification. This includes guidance on how to manage the lifecycle of data, such as how long to store data and when to move data from high-performance (and high-cost) storage systems to lower-cost archival systems. Manual data lifecycle management does not scale well, and it is prone to errors. Take advantage of cloud providers' data management tools to automatically migrate data to different storage systems or delete data that is no longer useful.
5. Performance management
Performance management in cloud computing focuses on monitoring applications and infrastructure resources to ensure you deliver expected levels of IT services and efficient usage of cloud infrastructure.
Application performance metrics vary depending on the application. Some common ones include:
- latency to retrieve data, load webpages or call an API function;
- number of database transactions per time period; and
- number of connected users.
Additionally, create alerts that notify application managers and support teams when a service does not function as expected.
Infrastructure monitoring is particularly important to control cloud cost. A key advantage of the cloud is the ability to scale and adjust resources to a workload's level -- at any point in time, you should have enough compute and storage resources to handle the existing workload and also avoid excessive unutilized resources. Monitoring tools and the cloud provider's autoscaling features can help you allocate cloud resources dynamically and efficiently.
6. Asset and configuration management
A big challenge for organizations is to maintain a dynamic array of cloud infrastructure resources within the bounds of what they expect to deploy. Developers and cloud engineers might manually deploy a VM for an ad hoc need and forget to shut it down -- that's not a big concern. However, teams should rely on controlled processes to deploy large clusters or use high-cost cloud services.
One way to manage infrastructure is to use infrastructure as code (IaC). Rather than have cloud engineers start and stop resources, IaC specifies what to run or deploy in your environment to support the application. The IaC application can then monitor the state of the infrastructure, which is distinct from the state of configuration. If it varies from the desired state, such as if some VMs fail, it can bring your infrastructure back to the desired state automatically.
Configuration management also helps an organization control the use and storage of secrets, such as credentials and encryption keys. Use centralized repositories to store secrets, rather than insecure practices such as login credentials in scripts or programs, which may be visible to anyone with access to the script.
Cloud governance models and standards
Several governance models and standards are relevant to cloud computing standards, although none are specific to the cloud. Governance models and standards are less about specific technologies and more about people and processes.
- COBIT is a governance standard created by the Information Systems Audit and Control Association to help businesses and other organizations manage IT operations. The model includes a framework of processes and practices, process descriptions, control objectives, management guidelines, and maturity models. COBIT is a generic governance approach that works well with other standards, such as ITIL.
- ITIL is a framework with detailed process descriptions to help businesses standardize how they select, deliver and maintain IT services, and strategically plan for new technology initiatives.
- ISO/IEC 38500 is an international standard for corporate IT governance that covers processes, communications and decision-making. The standard addresses how to define responsibilities; support IT operations, technology and related acquisitions; monitor performance; and conform with policies. It also helps businesses understand how users interact with applications and systems, and avoid creating incentives for users to bypass policies and procedures.
What are the challenges of cloud governance?
A major challenge of cloud governance is the breadth of topics to address. It is more practical to introduce a comprehensive governance framework incrementally, rather than in a single step. Start with the highest priority items for your organization -- in strictly regulated industries, compliance and security are top priorities. If your cloud spending is excessive and unsustainable, focus on cost management early in the process.
Automation is essential to governance. Cloud environments are dynamic and can scale to large numbers of resources, components and services. Take advantage of cloud service features that support governance, such as data lifecycle management policies that can help ensure data is stored in proper storage services and purged on a defined schedule. Use third-party tools, such as vulnerability scanners to check the contents of code repositories and pinpoint vulnerabilities in your applications.
Finally, governance is an ongoing effort with multiple processes. Governance frameworks such as NIST are useful starting points to help guide your organization's governance practices.







