
Getty Images/iStockphoto
How to create Amazon EC2 security groups
Before setting up security groups for AWS resources, review rules, requirements and potential missteps. Follow these steps to properly configure security groups for EC2 instances.
Network security is a key element in any application deployment, cloud-based or otherwise. AWS offers many tools to control which entities can access an organization's cloud resources.
For Amazon Elastic Compute Cloud (EC2) deployments, there are some foundational elements IT teams need to configure at the network layer:
- Virtual Private Cloud (VPC). A VPC is a virtual network where EC2 components are launched.
- Subnets. These provide a more granular grouping of components within a VPC and are linked to an Availability Zone. Subnets also configure network routing rules that regulate traffic flow externally or internally within the VPC.
- Security groups. EC2 security groups are, essentially, a network firewall and they control incoming and outgoing traffic for EC2 instances.
In order to launch an EC2 instance, IT teams need to link it with a VPC and a subnet, and they need to assign it at least one Amazon EC2 security group. Like any other AWS resource, security groups can be created and configured through the AWS Management Console, Amazon Command Line Interface (CLI) or SDK.
Amazon EC2 security group rules
There are two sets of rules for an Amazon EC2 security group: inbound and outbound. Inbound rules define the incoming traffic the security group allows. Outbound rules define the traffic permitted to leave the compute resource associated with the security group.
Each inbound rule consists of three key elements:
- Protocol. Network protocols the rule will allow, such as TCP and User Datagram Protocol.
- Port range. A specific port or a port range to allow traffic on.
- Source. A specific IP, IP range or other security groups that will be allowed access.
With a security group ID, any component -- such as an EC2 instance or AWS Lambda function -- that is assigned to a security group can access an EC2 instance through the specified port and protocol. This option provides greater flexibility, but it should be assigned with care to avoid opening access to too many components.
Each outbound rule consists of:
- Protocol. Same as inbound rules.
- Port Range. Same as inbound rules.
- Destination. Similar to the inbound rules for source, except it refers to a destination the security group allows traffic to go to.
Even though security groups are typically assigned to EC2 instances, there are other compute components that also require a security group, such as Amazon Relational Database Service instances, Amazon ElastiCache nodes, Amazon Redshift nodes and Amazon DocumentDB instances. IT teams can opt to link Lambda functions to a VPC, in which case they need to be assigned a security group.
Configure security groups in the most restrictive way possible and avoid situations where there a wide range of ports or IP ranges have access. There are Amazon cloud offerings, such as Amazon GuardDuty or AWS Trusted Advisor, which detect potential weaknesses and malicious traffic due to security group misconfigurations. Use these services to monitor Amazon EC2 security groups in an effective way to keep network security intact.
How to create a security group in AWS
IT teams can create a security group from the EC2 console and the CLI.
In the console, click on the "Security Groups" link in the left navigation bar and click on the Create security group button. It's important to note that security groups are assigned to a specific VPC.
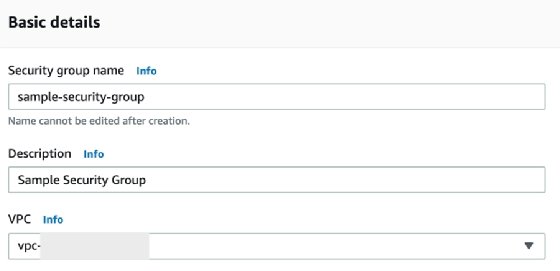
The next step is to configure the inbound rules. The example below allows traffic on port 22 from IPs in the 10.1.0.0/24 Central Identities Data Repository range. The source can also be configured as another security group, which allows traffic from resources that have the security group assigned to them.
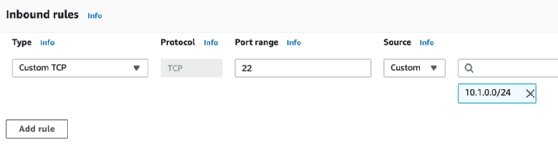
IT teams also need to configure outbound rules, which typically allow outgoing traffic without restrictions. Outbound rules can be set up to only allow traffic to specific IP ranges or security groups.
You can also create a security group via the CLI with these commands:
- AWS CLI. create-security-group
- AWS Tools for Windows PowerShell. New-EC2SecurityGroup







