
nobeastsofierce - Fotolia
Secure data in the cloud with encryption and access controls
Enterprises can't rely on their IaaS provider to protect sensitive information in the cloud. Implement these data security techniques to mitigate potential risks.
Cloud services offer various security features -- such as advanced configurations, automated encryption and access controls -- to protect your sensitive information. However, many organizations still fail to properly secure data in the cloud.
Enterprises can't leave the burden of data security to their cloud provider. Instead, they must take steps to properly implement and test a cloud security strategy. To get started, implement the following best practices.
Encrypt data
To secure data in the cloud, it's essential to encrypt it, whether in flight or at rest. To plan encryption needs, map out data flows through all applications and the tables that store the resulting data. Then, encrypt data the same way in storage and during a transfer.
Think of the levels of data encryption in terms of T-shirt sizes: small, medium and large:
- Small: A basic encryption plan for stored data, in which data may be compromised, but encryption ensures minimal damage.
- Medium: A plan that encrypts data in flight and at rest to help deflect breaches.
- Large: A more advanced plan that encrypts both data at rest and in flight, but also includes features such as tracking data usage by attributes and users and monitoring all changes to data.
In general, other best practices include the use of third-party tools to test and verify cloud security configurations and to identify any gaps that need to be addressed.
Manage access
Developers, architects and DevOps teams can implement several best practices to secure data in the cloud.
First, apply the same distributed access controls used for applications to data when it moves off premises or over the public internet. For example, if application access includes role-based access control, then add that same role-based security layer to control access to data. If possible, add federated identity management to verify every user at each interaction point and to track usage data. Within the application code, consider supporting verification of access to both the application and the data for each request. However, never specify the data location within the application code.
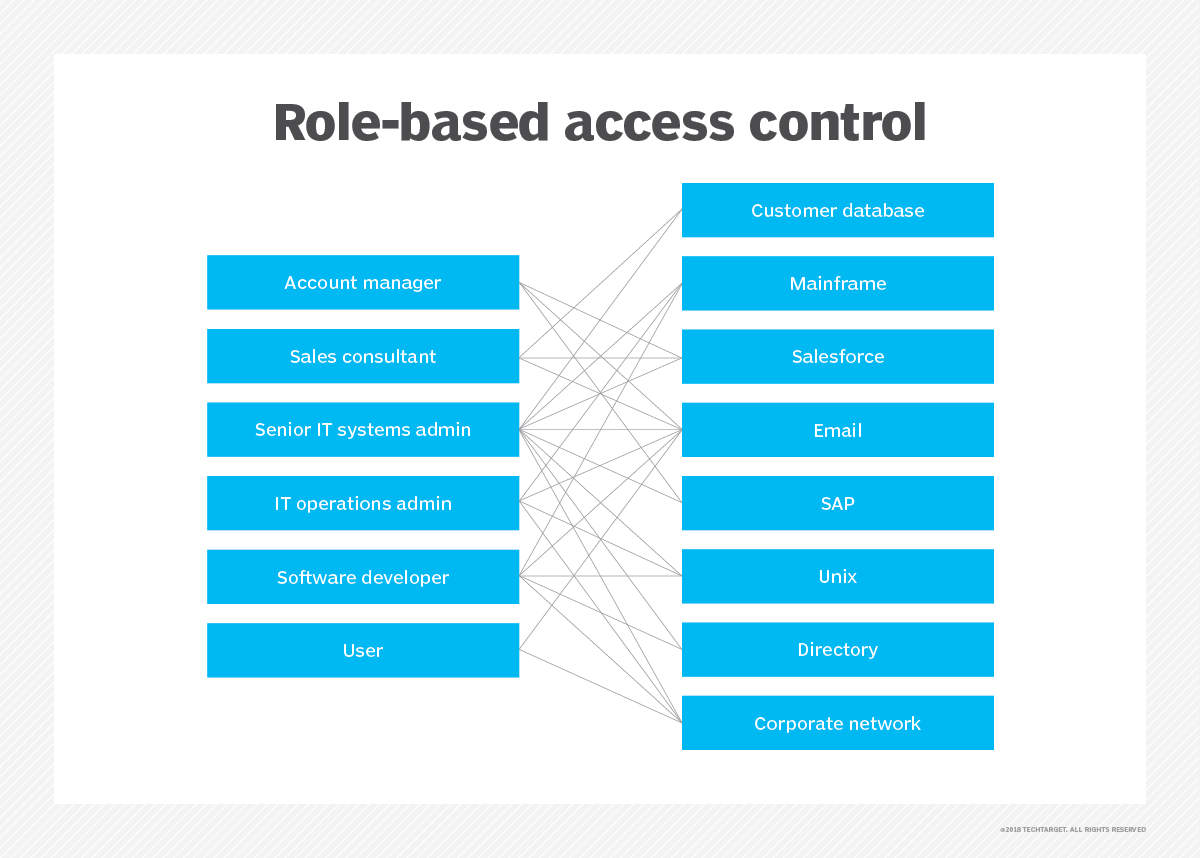
Also, centralize the management of data and application deployments and updates so that both use the same tools in similar ways and within the same control location.
When dealing with data from multiple customers, store that data separately so customers cannot access each other's data without proper authorization. Enterprises should work with their cloud provider to verify that customer data is separated, both at rest and while in motion.
Ensure any internal employees who use a computer or mobile device to access an organization's network have secure access, regardless of where they access that network from.
Lastly, to further secure data in the cloud, be cautious of any documents or apps that are shared among users. These shared cloud applications, which are easy to access and use, can put sensitive information at risk. Role-based access controls again ensure that only authorized users can access certain data. Track and monitor data usage to ensure access controls are effective.







